
Version: 1.02016-10-06National Information Assurance Partnership

| Version | Date | Comment |
|---|---|---|
| 1.0 | 2016-10-06 |
1. Introduction
1.1. Overview
1.2. Terms
1.2.1. Common Criteria Terms
1.2.2. Technology Terms
1.3. Conformance Claims
1.4. How to Use This Extended Package
1.5. Compliant Targets of Evaluation
2. Security Problem Definition
2.1. Threats
2.2. Assumptions
2.3. Organizational Security Policies
3.1. Security Objectives for the TOE
3.2. Security Objectives for the Operational Environment
3.3. Security Objectives Rationale
4.1. Security Functional Requirements
4.1.1. Security Audit
4.1.2. User Data Protection
4.1.3. Security Management
4.1.4. Protection of the TSF
4.1.5. Trusted Paths/Channels
4.2. Security Assurance Requirements
Appendix A: Optional Requirements
Appendix B: Selection-Based Requirements
Appendix C: Objective Requirements
Appendix D: References
Appendix E: Acronyms
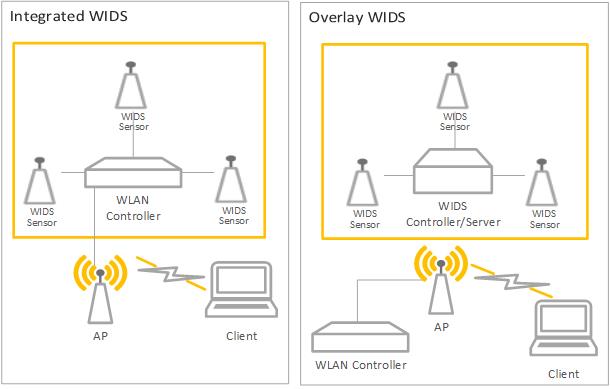 Figure 1: General TOE
Figure 1: General TOE | Threat, Assumption, or OSP | Security Objectives | Rationale |
| T.UNAUTHORIZED_DISCLOSURE_OF_INFORMATION | O.SYSTEM_MONITORING, O.WIDS_ANALYZE, O.WIPS_REACT | |
| T.UNAUTHORIZED_ACCESS | O.SYSTEM_MONITORING, O.WIDS_ANALYZE, O.WIPS_REACT, O.TOE_ADMINISTRATION | |
| T.DISRUPTION | O.SYSTEM_MONITORING, O.WIDS_ANALYZE, O.WIPS_REACT | |
| A.CONNECTIONS | OE.CONNECTIONS | |
| A.PROPER_ADMIN | OE.PROPER_ADMIN | |
| P.ANALYZE | O.WIDS_ANALYZE |
| SFR | Potential Security Violation. |
| FAU_INV_EXT.3 | Detection of authorized EUD establishing peer-to-peer connection with any other EUD. |
| FAU_INV_EXT.3 | Detection of EUD bridging two network interfaces. |
| FAU_WID_EXT.1 | Detection of rogue AP. |
| FAU_WID_EXT.1 | Detection of malicious EUD. |
| FAU_WID_EXT.2 | Detection of traffic with excessive transmit power level. |
| FAU_WID_EXT.2 | Detection of active probing. |
| FAU_WID_EXT.2 | Detection of MAC spoofing. |
| FAU_WID_EXT.3 | Detection of RF-based denial of service. |
| FAU_WID_EXT.3 | Detection of deauthentication flooding. |
| FAU_WID_EXT.3 | Detection of disassociation flooding. |
| FAU_WID_EXT.3 | Detection of request-to-send/clear-to-send abuse. |
| FAU_WID_EXT.4 | Detection of unauthorized authentication scheme use. |
| FAU_WID_EXT.5 | Detection of unauthorized encryption scheme use. |
| FAU_WID_EXT.5 | Detection of unencrypted traffic. |
| Table 1: Potential Security Violations. |
| Requirement | Auditable Events | Additional Audit Record Contents |
| FAU_ANO_EXT.1.1 | None | None |
| FAU_ANO_EXT.1.2 | None | None |
| FAU_ARP.1.1 | None | None |
| FAU_ARP_EXT.2.1 | None | None |
| FAU_GEN.1.2/WIDS | None | None |
| FAU_IDS_EXT.1.1 | None | None |
| FAU_INV_EXT.1.1 | None | None |
| FAU_INV_EXT.1.2 | None | None |
| FAU_INV_EXT.1.3 | None | None |
| FAU_INV_EXT.2.1 | None | None |
| FAU_INV_EXT.2.2 | None | None |
| FAU_INV_EXT.2.3 | None | None |
| FAU_INV_EXT.3.1 | None | None |
| FAU_INV_EXT.4.1 | None | None |
| FAU_INV_EXT.4.1/CELL | None | None |
| FAU_INV_EXT.5.1 | None | None |
| FAU_MAC_EXT.1.1 | None | None |
| FAU_MAC_EXT.1.2 | None | None |
| FAU_SAA.1.1 | None | None |
| FAU_SAA.1.2 | None | None |
| FAU_SIG_EXT.1.1 | None | None |
| FAU_STG_EXT.1.1/PCAP | None | None |
| FAU_STG_EXT.1.2/PCAP | None | None |
| FAU_STG_EXT.1.2/pcap, | None | None |
| FAU_STG_EXT.1.3/PCAP | None | None |
| FAU_WID_EXT.1.1 | None | None |
| FAU_WID_EXT.1.2 | None | None |
| FAU_WID_EXT.2.1 | None | None |
| FAU_WID_EXT.2.2 | Sensor wireless transmissions capabilities. | Wireless transmission cappabilities are turned on. |
| FAU_WID_EXT.2.3 | None | None |
| FAU_WID_EXT.2.4 | None | None |
| FAU_WID_EXT.3.1 | None | None |
| FAU_WID_EXT.4.1 | None | None |
| FAU_WID_EXT.4.2 | None | None |
| FAU_WID_EXT.5.1 | None | None |
| FAU_WID_EXT.5.2 | None | None |
| FAU_WID_EXT.5.3 | None | None |
| FAU_WID_EXT.6.1 | None | None |
| FAU_WID_EXT.6.2 | None | None |
| FAU_WID_EXT.7.1 | None | None |
| FAU_WIP_EXT.1.1 | None | None |
| FDP_IFC.1.1 | None | None |
| FMT_SMF.1.1/WIDS | None | None |
| FPT_FLS.1.1 | Information about failure. | Indication that there was a failure, type of failure, device that failed, and time of failure. |
| FPT_ITT.1.1 | None | None |
| FTP_ITC.1.1 | None | None |
| Table 3: Auditable Events |
| SFR | Management Function |
| FAU_ANO_EXT.1 | Specification of periods of network activity that constitute baseline of expected behavior (optional). |
| Table 2: Management Functions |
This EP does not define any SARs beyond those defined within the NDcPP. It is important to note that a TOE that is evaluated against this EP is inherently evaluated against NDcPP. When evaluating the TOE, it is necessary to apply the SARs defined for the base PP to the entire TOE and not just the portion that is described by the base PP.
throughput ([assignment: data elements (e.g. bytes, packets, etc.) per time period (e.g. minutes, hours, days)]),
time of day,
frequency; ,
thresholds,
[assignment: other methods]
] and the following network protocol fields:| Requirement | Auditable Events | Additional Audit Record Contents |
| FAU_ANO_EXT.1.1 | None | None |
| FAU_ANO_EXT.1.2 | None | None |
| FAU_ARP.1.1 | None | None |
| FAU_ARP_EXT.2.1 | None | None |
| FAU_GEN.1.2/WIDS | None | None |
| FAU_IDS_EXT.1.1 | None | None |
| FAU_INV_EXT.1.1 | whitelisted devices information | Type of device (AP or EUD), MAC Address. |
| FAU_INV_EXT.1.2 | None | None |
| FAU_INV_EXT.1.3 | None | None |
| FAU_INV_EXT.2.1 | None | None |
| FAU_INV_EXT.2.2 | None | None |
| FAU_INV_EXT.2.3 | None | None |
| FAU_INV_EXT.3.1 | Unexpected behavior by whitelisted device alert | Description of behavior detected (i.e., bridge, ICS connection), MAC address of whitelisted device, MAC address of the device that the whitelisted device made a connection with, connection start and end. |
| FAU_INV_EXT.4.1 | Information on location of device | Device MAC address, device type, classification of device, sensors that detected device, signal strength as received by detecting sensor(s), proximity to detecting sensor(s) (in meters). |
| FAU_INV_EXT.4.1/CELL | Information on location of device | device MAC address, device type, classification of device, sensors that detected device, signal strength as received by detecting sensor(s), proximity to detecting sensor(s) (in meters). |
| FAU_INV_EXT.5.1 | Alert generated by detection of rogue device. | Description of alert, type of device (AP or EUD), MAC Address, associations made between authorized devices (which APs are EUDs connected to), channel detected on, RF Band detected on, encryption type used by rogue, IEEE 802.11 standard used (a, b, g, n, ac), SSID (if AP). |
| FAU_MAC_EXT.1.1 | Alert generated by detection of mac spoofing. | Description of alert, type of device (AP or EUD), MAC Address, associations made between authorized devices (which APs are EUDs connected to), channel detected on, RF Band detected on, encryption type used by rogue, IEEE 802.11 standard used (a, b, g, n, ac), SSID (if AP). |
| FAU_MAC_EXT.1.2 | Alert generated by detection of mac spoofing. | Description of alert, location as labeled by administrator, time elapsed between connection in different locations, type of device (AP or EUD), MAC Address, associations made between authorized devices (which APs are EUDs connected to), channel detected on, RF Band detected on, encryption type used by rogue, IEEE 802.11 standard used (a, b, g, n, ac), SSID (if AP). |
| FAU_SAA.1.1 | None | None |
| FAU_SAA.1.2 | None | None |
| FAU_SIG_EXT.1.1 | Alert generated by violaton of user defined signature. | Name of alert being triggered(as provided when creating the signature), description of alert (as provided when creating the signature), MAC address of devices involved. |
| FAU_STG_EXT.1.1/PCAP | None | None |
| FAU_STG_EXT.1.2/PCAP | None | None |
| FAU_STG_EXT.1.2/pcap, | None | None |
| FAU_STG_EXT.1.3/PCAP | None | None |
| FAU_WID_EXT.1.1 | None | None |
| FAU_WID_EXT.1.2 | None | None |
| FAU_WID_EXT.2.1 | None | None |
| FAU_WID_EXT.2.2 | None | None |
| FAU_WID_EXT.2.3 | Details about what SSIDs are set as authorized. | SSIDs set by administrator as authorized. |
| FAU_WID_EXT.2.4 | Unauthorized activity | description of violation (i.e. whitelisted EUD connected to unauthorized SSID), identity information of the devices involved. |
| FAU_WID_EXT.3.1 | Alert generated for DoS. | MAC Address, device type, and classification AP or EUD attacked, DoS details (RF or injection based), for injection-based, indicate type (i.e., deauth flood). |
| FAU_WID_EXT.4.1 | None | None |
| FAU_WID_EXT.4.2 | Information about devices and unauthorized authentication methods. | MAC Address, device type, and classification of devices involved, authentication method used. |
| FAU_WID_EXT.5.1 | None | None |
| FAU_WID_EXT.5.2 | Information about devices and unauthorized encryption methods. | MAC Address, device type, and classification of devices involved, encryption method used. |
| FAU_WID_EXT.5.3 | Information about devices involved. | MAC Address, device type, and classification of devices involved (sending and receiving devices). |
| FAU_WID_EXT.6.1 | Information about detected devices. | Frequency band, channel used within frequency band, identification information (MAC address if applicable or other similar unique ID), device technology (i.e.,cellular), sensor(s) that detected devices. |
| FAU_WID_EXT.6.2 | None | None |
| FAU_WID_EXT.7.1 | None | None |
| FAU_WIP_EXT.1.1 | Information about action taken. | description of violation,the type of containment used, was containment triggered manually or automatically, sensor performing the containment (if wireless), details about the device (s) being contained (classification, device type, MAC address). |
| FDP_IFC.1.1 | None | None |
| FMT_SMF.1.1/WIDS | None | None |
| FPT_FLS.1.1 | None | None |
| FPT_ITT.1.1 | None | None |
| FTP_ITC.1.1 | None | None |
| Table 4: WIDS/WIPS Auditable Events |
| Identifier | Title |
|---|---|
| [CC] |
|
| [CEM] |
| Acronym | Meaning |
|---|---|